From Demos to Pentests: Overcoming Challenges in my (ongoing) Cybersecurity Journey
I quit I said, buuuut...
This might be a long one, which I’ve been going back and forth on the past few days after reflecting on my post “I quit IT” on LinkedIn and since then have been having this blogpost in the back of my head, where I’ve been thinking a lot about where I want to go with my career. Not changing role yet or anything- but I want to make sure I stay proactive, and do something that will keep me learning more.
Technical Presales Background
I still remember the day 5 years ago, when I got the call from an Irish number that I didn’t recognize, and almost didn’t answer (I tend to not answer my phone if I’m not expecting a call) - where the recruiter from Microsoft, called me out of the blue saying he saw my profile on LinkedIn and might have a position for me at Microsoft Ireland.
As you might imagine, I didn’t believe this at first, and I was also a Senior Consultant for a Microsoft Partner and at a customer site working on a project, thinking this was some kind of joke, almost hanged up on them, but for some reason I didn’t and told them to call me again later that day, when I was not busy deploying Intune and everything that came with it.
Said and done, they did call later that day and we discussed the role; Technical Specialist, it was called. What it really meant at the time, didn’t click for me but it was for Microsoft and it was in Ireland, where I wanted to move back to at the time.
A handful calls and interviews, both technical and non-technical (and the mandatory technical challenges for the tech interview of course), Some difficult conversations with my current manager at the time and lack of interest in a Teams Project, I did get an offer letter for the position during my vacation in Philippines (which one day I’d love to explore more, not just Manilla).
Fast forward a few months and a bunch of flights to move stuff, from this weather-
 Norway in the cold freezing February.
Norway in the cold freezing February.
To this and me standing in front of the Microsoft building (a cold February morning, very confused on how to get there, so I basically just followed the flow of people)
 Same day in Ireland. Where it supposedly only snowed every other decade.
Same day in Ireland. Where it supposedly only snowed every other decade.
 First day at Microsoft required a obligatory picture of the sign
First day at Microsoft required a obligatory picture of the sign
 In the Microsoft Dublin HQ. The colored floor is LED based.
In the Microsoft Dublin HQ. The colored floor is LED based.
It was… surreal to say the least. Me, who dreamt at working at Microsoft (and failing a technical interview as the Premiere Field Engineer/Customer Engineer/Cloud Solution Architect (this role had a lot of name changes over the years) for Office 365/Exchange few years prior - which sounded like my dream role, and still wanting to get into the role of a CSA as it’s called today
But I made it. I was officially a Full Time Employee (FTE) at Microsoft Ireland. This is coming from someone who learned the hard way (and diagnosed in the mid 30s) that I have General and Social Anxiety (that explains the panic attack(s) I get when I used to go to the office), major depression disorder and ADHD (inattentive).
Skills developed in presales role
I’m sure I will come back and revise this one day, with some actual skills that you get from this role.
While this will not specifically spell out what skills I’ve learned thus far, as a Pre-Sales Engineer (or Technical Specialist, Security if we are using the official title), I do hope it breaks down a little what it means and how to approach this role, in my opinion.
Primary technical point of contact for potential customers during the sales process
What this really means is the customer will try use you as your go to person for technical challenges and issues. How do we deploy this? Can you do it for us? Why is this not working? and this is where the role as the Technical Specialist (remember, pre-sales role!) you need to be firm, yet friendly remind the customer on what you can do, and cannot do. You have to be able to say no, draw the line on when to introduce other teams that handle the aspects of deployment and troubleshooting and refer to documentation available online. OR even refer them to the Unified Support if they have that (if not, great uspell opportunity!)
You’re not the customers personal contact around everything tech related. However, in the end you need to be the one who decides to where you dedicate your time, can you turn it into a opportunity to upsell, will it drive the sale cycle forward? Will you remove technical blockers? In that case, it might be worth investing some time into it.
Deep technical understanding of cloud security architectures, solutions/technologies including Microsoft M365 Defender, Defender for cloud and Sentinel and expertise in extended detection and response (XDR), zero trust and cloud security solutions and architectures
Basically, embrace the learn it all, don’t be fooled by the know it all thinking. As the Technical specialist you really need to understand the ins- and outs of the product(s) but at the same time, there is no way you can be an expert on all the products (depending on role), which in some cases sums up to about 87 products give or take. Nobody expect you to be a expert on 87 products (again, depending on role).
Remediate blockers; leads and ensures technical wins for Microsoft Security and adjacent technologies. Engages with and reaches out to customers proactively and independently; builds credibility with customers as a trusted advisor for Microsoft Security; and searches for and uses Microsoft Security customer references; and facilitates handoff to customer success for post sales deployment.
This one can be tricky, you have a lot of tools available for you, leads being the clues on what customers has today, and how from a Microsoft perspective you could win them over by removing technical blockers such as, save the customer money but migrating, show how easy it is to deploy the solution, what their ROI (Return on Investment) would be, how can the security team focus on other tasks. Bascially, how can the IT Team focus on tasks that are more important, how can the customer spend less money but increase their efficiency.
It also states you are the trusted advisor (and this will be mentioned a lot), so if we look back on point one, this is a still a pre-sales role but you are their technical advisor providing them details on how to do things, or show them how it works, be their brainstorm buddy, and then also involve other teams that are available to you or even partners.
Develop strategies and recommendations to improve the client’s security posture, shapes technical win plan and tailors Microsoft messaging to audience for security opportunities. Enhances team capabilities for extended detection and response (XDR), zero trust and cloud security and develops differentiated compete strategies for Microsoft Security for assigned customers.
This is where you as the technical seller are really, selling. You are creating the story on how the products can save the security team time and effort by automating and enhancing their capabilities, turning a junior analyst to a senior one with the help of the tools provided in the XDR Suite.
In the end, what’s important is that you listen to the customer, you don’t sell them on something they are not ready for, and make sure it’s their trust you gain first and foremost. In short, be the technical advisor, don’t push the solution on them, but do show how it could be a win-win situation.
Lead technical presentations, demonstrations, workshops, architecture design sessions, explain, demonstrate, and architect the solution to help solve customer security challenges and priorities.
To my, this is one of the more fun aspects of the job, leading the technical discussion you need to actively listen to what the customer has to say, be ready to demo something on the fly, so it means you need to have prepared your environment beforehand and made sure things work (and take precautions in case it does not).
or say you even lead internal/external workshops, one -to-many webinars about something that is related to your focus and prove the value that way. It can also be that you need to help the customer in question figure out “where do we go from here?” in the architecture design sessions and once again, show how it solves the challenges the customer are facing, or even in some cases - simply consolidate the products to save money.
Drives cross-workload support for Microsoft solutions for security. Leverages insights and coaches’ teams to align new or changing technology to customer security needs.
You’ll work with a lot of people in the role of a Technical Specialist. Be flexible (say no when it makes sense, or you will get overwhelmed) but be open to teach other about new features and solutions, including partners. Don’t be afraid to reach out to others within the organization to see how they have tackled certain challenges. I’ve never had anyone say no when I asked, and if they did- they would offer an alternative timeslot.
Responsible for engaging with other teams within and outside the organization throughout the sales cycle. Engaging partners in sell-with scenarios and supporting their technical capabilities is key to scaling solution delivery.
Speaking of partners. Engage with them early and often, make sure you involve them as soon you can, double check with the customer who their preferred partner is, and reach out to them and set up syncs. This will help a lot in both you networking with the partners, both sides leveraging the technical expertise and helping finding solutions to challenges.
Understanding customer environments
My day(s) are (roughly outlined) preparing for customer calls, researching what they have, what they are using today (most of the time, we simply ask, but it hit me, I can use the OSINT (Open Source Intelligence to gather some more info, for example what systems are they using).
Then prepare some presentations, both in PowerPoint and in a demo environment (I personally lean more towards demo environment and showing things live, rather then death by PowerPoint) which leads to answering questions, praying to the demo gods and hope you poured out enough coffee for them (demo gods, not the customer), trying to not forget the story you want to tell in your demo- showing the customer the value on the product. So very sales based kind of thinking in a way, with some sprinklings of Technology on top of it.
 Basically how I feel after every customer call, thank you (General & Social) Anxiety & Introvert-ism (is that a word even?).
Basically how I feel after every customer call, thank you (General & Social) Anxiety & Introvert-ism (is that a word even?).
When the demo is done, make sure you took notes (or remembered to turn on Copilot recording/transcription, if you did- you thanked yourself later) and put them into the CRM System, basically you logging your activity like you do in a helpdesk role, when creating or updating a ticket, the more mundane yet really important admin work. Similar to a helpdesk role, if the information is not in the ticketing/CRM System, it didn’t really exist (and you are tracked on it, usually YMMV).
Then then more fun part(s) of the role, you skilling up on the products you present to the customers, learning something new - the hands-on stuff.
- learn more about how they work,
- what challenges customers face,
- how to implement the technology,
- what are the best practices,
- what change management do you need to think about?
- What’s new and upcoming?
- Building your own lab,
- Breaking your own lab,
- panic and run around in circles you broke your lab,
- vent to your colleague you broke your lab and not sure what to do
- figure out why the lab broke,
- document the fixes (I’m serious, this is huge) and share with your team.
- See step one.
Decision to transition to security
Okay, so we know how I (in a TL;DR-ish way) landed my dream gig (it isn’t) and got to Microsoft, what changed? Well, technically not much… however!
I always wanted to specialize in something, and in a way security were always there, however I never really dove into it until I felt there was no growth at the time being a Technical Specialist Modern Work (this was when we didn’t have the focus on Security) - I was seen as an Intune Subject Matter Expert, which I wanted to be recognized as (yay!), but there was no real path forward in my role, besides becoming a manger or changing role completely, which is difficult enough as it is, you might be on the inside and working for Microsoft, but internal hiring is difficult since you’re still competing with internal and external applicants.
I was asked if I wanted to be more on the Sales sides of things, a Solution Sales Specialist (SSP) and that was a huge no-go for me, money might be better in the end, but it would not bring me the technical aspects of the job that I really enjoyed and loved, so I kept at it, continuing as the Modern Work Technical Specialist.
This went on until I learned we introduced the Security Compliance & Identity role, which branched off focusing on, theSCI role (now more known as the Security Technical Specialist) was offered in EMEA (Dublin in my case) but at first I didn’t start applying for it, as I had told my manager I wanted move to North America, so I wanted to focus on roles in US, and instead of trying to land a role in EMEA I started applying to roles with Security focus, as I felt this was a huge step forward, and it took me to places I wanted to be (North America), so I could be with my, now wife.
It took time, but I did manage to land multiple interviews (and fail some of them, I like to think ainly due to immigration and visa reasons, sponsoring is expensive and time consuming.) as a Security Technical Specialist, I finally landed my role with Microsoft as a Security Technical Specialist, which is, when we really break it down, a technical advisor (with focus on selling the product) for the Microsoft Security products in Microsoft 365 and Azure.
Intune was always my go to area, with mobile deployments and cloud endpoints, and I still love that, but working with security focused areas and learning more about both Blue and Red Teaming and Ethical Hacking have really sparked the interest to learn more about this area, and that’s basically how I just dived deep into the decision to somehow, some day transition out of my role in the Pre Sales _(which I never thought I would ever work in, IT yes, but IT-Sales related jobs? Never) _to a more ‘technical’ role, such as a Pentester, or something similar that is more hands on. Does that mean I regret my choice trying this out, working in pre-sales? Not at all! If anything I have grown from it. I looked the shark in the mouth and I jumpede anyway. Still here, take that!
Who knows, maybe I even stay in the role within the sales but shape it to more what I want, which would be more hands-on and practical things, not setting up a demo from some pre-configured environment or just running a click-through demo. Granted there are times we have to do that, but it doesn’t mean we don’t get down and dirty in the products, if I really want to learn a product I need to set it up, figure out how it works, what doesn’t work etc.
I do find the Security/Pentesting route incredibly rewarding and enjoyable, I’ve taken multiple classes virtually and self-phased courses (as mentioned in other posts) to learn more, tinkering in my home lab on setting up things from scratch and that’s where I really think my passion are within security, where I can do hands-on projects and help educate others, making them safer in the progress, and show that security is a marathon and not a sprint.
Early Certification Struggles
Systems Security Certified Practitioner certification attempts
Twice now, I have failed the Systems Security Certified Practitioner (SSCP) Exam. I don’t enjoy nor even remotely think the ISC(2) exams are well made for the purpose of an so called entry level exam. I am dissapointed in myself, however I try to learn from mistakes, I was definitely overconfident, and the resources I used was clearly not enough, so it’s back to the books for me on this one.
Impact on confidence
To put it simply, it almost made me quit everything IT Related. I have taken many certifications ranging from fundamentals to expert level (this is debatable, but that’s the naming of it), and while I failed at times, it didn’t bring me down (yes, I was disappointed I didn’t pass, but not ‘I-quit-this-field’ kind of way).
When it really comes down to it, I personally think that
- I’m not good nor enjoy multiple choice exams. (I feel okay at some, but ISC(2) and their tests are definitely not one of them)
- The wording in the exam(s) (especially in the ISC(2) exams) are very vague and designed to really throw you off
- It (again, ISC2) doesn’t (if you ask me) measure your skills, besides taking in account you remember how specific things works. I strongly believe people will look it up via Copilot or other means these, including the source before recommending something.
So as mentioned at the start of the post, I wrote on LinkedIn that I feel like a fraud and was considering quitting the field of IT. To say the least, I was not in a good space mentally, told my manager I needed a day off and stayed in bed overthinking things.
I was surprised about the support I got, people reached out on LinkedIn, on Teams, over phone to make sure I was doing okay.
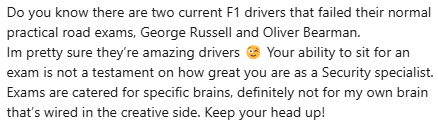
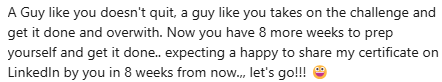
For examples from LinkedIn I got comments like these:
Well, they are not wrong, I didn’t quit - nor do I want to. I had a really bad day, but if we fall, we get up again. That said, I don’t know for certain I will pass the exam in 8 weeks (but boy do I hope so, it is part of my degree and I need the class completed)
Learning from failures
I know for a fact, I’m not a person who’s good at taking tests, I get test anxiety, overthink the answers and probably rushes through tests to get it over with. At least multiple choices tests. I’m curious to see how I do in practical tests, where you write a report on your findings, not only does it reflect how it works in the field, but it does not judge you on knowing very specific answers, like in the ISC(2) exams where the questions are incredibly vague and answers are no different. Doing classes with WGU, where I write papers or when I write documentation, step-by-step instructions on how to configure something, or helping teaching someone about the product I’ve successfully deployed in my own environment, What did I find, how did I find it, how did I resolve it? that’s when it’s really impactful and rewarding.
To me, that is definitely a better way to show your passion and understanding of the products or topics, even if at times, it really blows spending all the time writing the essay, report, documentation or similar because you’re stuck. This is also a reason why I created the blog, or so I like to think, bit for my own need to share my documentation when I get around to it (and have a place I can go back and remind myself how I did things) and to share my general thoughts and experiences.
Building New Foundations
WGU academic journey
So far, Western Governors University (WGU) is still a great school. I haven’t had any issues with their proctoring system (knock on wood). The classes are useful, especially if you really take time to dig into the content that are offered and it’s something I am fortunate enough that my job reimbursed me for it.
Some of the technical classes do offer hands-on labs and they are quite fun, and the major benefit of the school (highly depending on your program, I should add) is the cost and certifications. As the time of this post, the Cybersecurity & Information Assurance (BSCAIA) the program cost $4,365 per term, which is less than what I paid for total time in college trying to get a Associate Degree in Professional Photography (spoiler: I dropped out, and heavy in student debt due to it) and in my case, the BSCAIA (I’m not sure if this is the accurate acronym, but we’re going with it) program offers opportunities to earn certificates such as:
The following certifications are related to classes :
Some of these classes can be taken elsewhere, such as Study.com or Sophia.org - doing so will not give you the vouchers though, so keep that in mind.
CompTIA:
- A+ IT Foundations - D316 & IT Applications - D317
- Network+ - Networks - D325
- Security+ - Network and Security - Applications - D329
- Project+ - Business of IT - Project Management - D324
- CySA+ - Cyber Defense and Countermeasures - D340
- PenTest+ - Penetration Testing and Vulnerability Analysis - D332
These CompTIA certifications are considered Stackable certifications, meaning they are tied into you passing the above certifications in some form.
- IT Operations Specialist (Stackable certification)
- Secure Infrastructure Specialist (Stackable certification)
- Network Security Professional (Stackable certification)
- Network Vulnerability Assessment Professional (Stackable certification)
- Security Analytics Professional (Stackable certification)
Linux Professional Institute:
• Linux Essentials - Linux Foundations - D281
ISC(2)
- Certified Cloud Security Professional (CCSP) – Optional Voucher - Managing Cloud Security - D320
- Systems Security Certified Practitioner (SSCP) – this is your Information Systems Security - C845 class
Axelos:
- ITIL Foundation Certification - Business of IT – Applications - D336
TCM Security training experience
One of the main reasons why I really enjoy the TCM Security, is the practical aspects of their training, they mix the video based courses with hands-on practical elements in their training, which to me is invaluable and a huge advantage in their favor.
I have said it before and I will yell at the clouds around this, their pricing are unbeatable for what you get. Their annual all-inclusive subscription? $299.99/year - that is a lot of content for you to really dive into and learn from, it goes from foundational to blue team and red teaming. Never programmed? No worries there is beginner courses around it. Linux? Some great courses around it too!
Attack Defend Active Directory course insights
This was a one day class instructed by Heath Adams the CEO of TCM Security. I could definitely draw comparisons to the CQURE Advanced Windows Security Course, but personally found a lot more value out of this class.
Here is what the Active Directory live class included:
Active Directory Overview
What is Active Directory? Physical Active Directory Components Logical Active Directory Components
Pre-Compromise AD Attacks and Defenses
LLMNR Poisoning Attacks and Defenses SMB Relay Attacks and Defenses IPv6 Attacks and Defenses AS-REP Roasting Attacks and Defenses Passback Attacks and Defenses Inside the Attacker’s Mindset
Post-Compromise AD Enumeration
Understanding common mistakes from an Administrator’s perspective** Reviewing common enumeration tools, such as: Bloodhound, Plumhound, Pingcastle, ldap domain dump, and much more Understanding common mistakes from an Administrator’s perspective
Post-Compromise AD Attacks and Defenses
Pass Attacks and Defenses Kerberoasting Attacks and Defenses Token Impersonation Attacks and Defenses URL File Attacks and Defenses GPP Attacks and Defenses Credential Dumping Attacks and Defenses Persistence Attacks and Defenses Inside the Attacker’s Mindset – Revisited
AD Case Studies Real case studies from real pentests AKA “How they got owned”
Practical Skill Development
Weekly Hack The Box commitment (or attempt to)
Something I should have done a long time ago, is to actually set proper goals when it comes to the Hack the Box and other services. Thankfully I have some perks from work, that helps me getting the annual subscription at no cost (well it’s reimbursed - but hey, it’s a perk!)
I started off on one of the paths but then I kinda, dwindled out? So it’s something I plan on starting getting back to, doing at least something to completion (or make progress) each week, to both fulfill the sense of progress, but learning something new and enhance my skills.
Current Progress and Challenges
Some of the classes are incredibly fun - others, you may have guessed it, not so much. The current class I am attending (besides the SSCP class, more on that further down), called D333 Ethics in Technology is one of these classes I find, incredibly dull and boring. I understand the theory behind it, but the requirement to memorize certain laws and regulations only to pass the class is really slowing me down.
That said, I think I am doing good progress on it and hopefully soon I can mark it as complete and move onto more interesting classes. One is being cryptography, which I feel is another subject I don’t find the most interesting but definitely worth taking, so hopefully it will be interesting.
I know one of the classes, will offer an option to take the Cloud Security Certification - CCSP - Certified Cloud Security Professional exam by ISC(2) and I will likely try once I’m ready, since WGU is offering me a voucher for it.
Maintaining motivation through setbacks
Something I struggle with, is getting started - I know I want to do it, I have the tools but it’s so easy to just not do it. Heck, as I’m writing this post, I’m technically procrastinating another post around my homelab environment (and fixing up my rack, and 3D Printing the modular racks.. you get the drift) around setting it up and configuring it for use.
So I asked Copilot on it, to gather my thoughts (I personally find copilot very helpful) and here is what they came up with.
Set Realistic Goals: Break down your larger goals into smaller, manageable steps.
Stay Positive: Focus on what you’ve accomplished, rather than what you haven’t.
Learn from Setbacks: Treat setbacks as learning opportunities, not failures.
Seek Support: Talk to friends, family, or mentors who can provide encouragement.
Stay Flexible: Be open to adjusting your plan if necessary.
Celebrate Progress: Reward yourself for the small victories along the way.
Stay Persistent: Keep your long-term vision in mind and don’t give up.
Practice Self-Care: Ensure you’re taking care of your physical and mental well-being.
As well some other ideas I asked for on how to tackle motivation when there seems to be none:
Break Tasks Down: Divide tasks into smaller, more manageable pieces to make them less overwhelming.
Use Timers: Set a timer for short bursts of focused work (e.g., 25 minutes) followed by a short break.
Minimize Distractions: Create a clutter-free workspace and eliminate potential distractions.
Create a Routine: Establish a daily routine to provide structure and consistency.
Focus on the Present: Concentrate on one task at a time and avoid worrying about the future.
Engage in Activities: Participate in activities that you enjoy and that make you feel good.
Stay Flexible: Adjust your plans as needed, and remember that it’s okay to have setbacks.
Future Steps
Certification strategy after SSCP
I know for a fact, I need to take the CompTIA IT Certifications - PenTest+ (Plus) Certification Training for my degree with WGU, from my understanding this one is a mix between being multiple choice questions and having some practical elements, and I feel I have a better grasp on how they want me to answer and I feel the exam itself is more interesting compared to the SSCP.
While I don’t have to take the CYSA+ Certification for the Bachelor’s degree, I am considering taking it either way.
More importantly, the practical experience is something I want to dive deeper into, so with that said.
Practical experience goals
I was going to mention the Practical SOC Analyst Associate (PSAA), Practical Junior Penetration Tester (PJPT) and Practical Network Penetration Tester (PNPT) by TCM Security in the previous point, but I felt it leans into this one pretty strongly.
The PSAA, PJPT and PNPT are the three certifications I want to really focus on after I’m done with WGU and officially graduated, since they are more hands on learning (again, love it) and the tests are practical in nature, where you have to find everything and write a report on it, and present it.
As I already attended the AD Attack & Defend Live Class by TCM Sec. I feel confident I will enjoy the content, just from that single day I learned a bunch of things and it is in a way, preparation for the PJPT and PNPT certifications.
I did purchase their Professional Pentester Bundle Black Friday deal that provided certifications vouchers and training for:
Practical Junior Penetration Tester (PJPT) Practical Network Penetration Tester (PNPT) Practical OSINT Research Professional (PORP) Practical Career Ready Professional (PCRP) Practical Web Pentest Associate (PWPA) Practical Web Pentest Professional (PWPP)
That and I still have the Microsoft Cloud Attack & Defense Bootcamp by PwnedLabs to complete, which very similar to the TCM Security certifications, are a practical exam where you have to write a report on it.
And of course, continue to use my homelab for trying things out, building that cybersecurity lab with vulnerable machines, figure out some projects to learn Python and C# better, use various services such as Hack The Box, LetsDefend etc and doing CTFs (How to Start Capture the Flag (CTF) - TCM Security)
Career development plan
I am really bad when it come to the Career Development Plan. Like really really bad. I don’t like filling it out, I always struggle on what to put down and I feel I can never figure out what I want out of it. That said, I do have some plans - like the certifications and hands-on experience through labs and projects.
One day, I will get it all down on paper and be able to present it to my manager. But that’s for another day.
Summary
So in the end, I won’t quit IT or changing role (for now at least). I’ve had jobs in the past that I know will make me feel bored after a month or two, even if it sounds something I initially could see myself do for a period of time. Yes, I am really bummed out I didn’t pass the SSCP exam, but when it comes down to it, I’m sure I will pass it one day, hopefully next time I take it! But IT is a field I enjoy a lot and definitely feel there are areas of growth and really, a lot of different areas I can dive into if I want to try something new.
For now however I’m going on vacation where I will play boardgames with my friends and just have fun.